Terraform Implementation – Best Practices

Share This Article
Table of Contents
Subscribe to Our Blog
We're committed to your privacy. SayOne uses the information you provide to us to contact you about our relevant content, products, and services. check out our privacy policy.
These are times when cloud infrastructure is indispensable to businesses, both large and small. Because of this, numerous tools are now available that help companies manage their rapidly expanding cloud footprint. One of the most popular and handy cloud tools developed in the last decade has been HashiCorp’s Terraform. In this blog, we attempt to introduce a few Terraform best practices that will make for its proper implementation.
What is Terraform?
Terraform is a tool that provides an abstraction layer for both describing and provisioning different types of cloud infrastructure. It works on all the major and popular Cloud providers, including AWS, Azure, IBM Cloud, Google Cloud, and also on on-premises cloud frameworks such as VMWare.
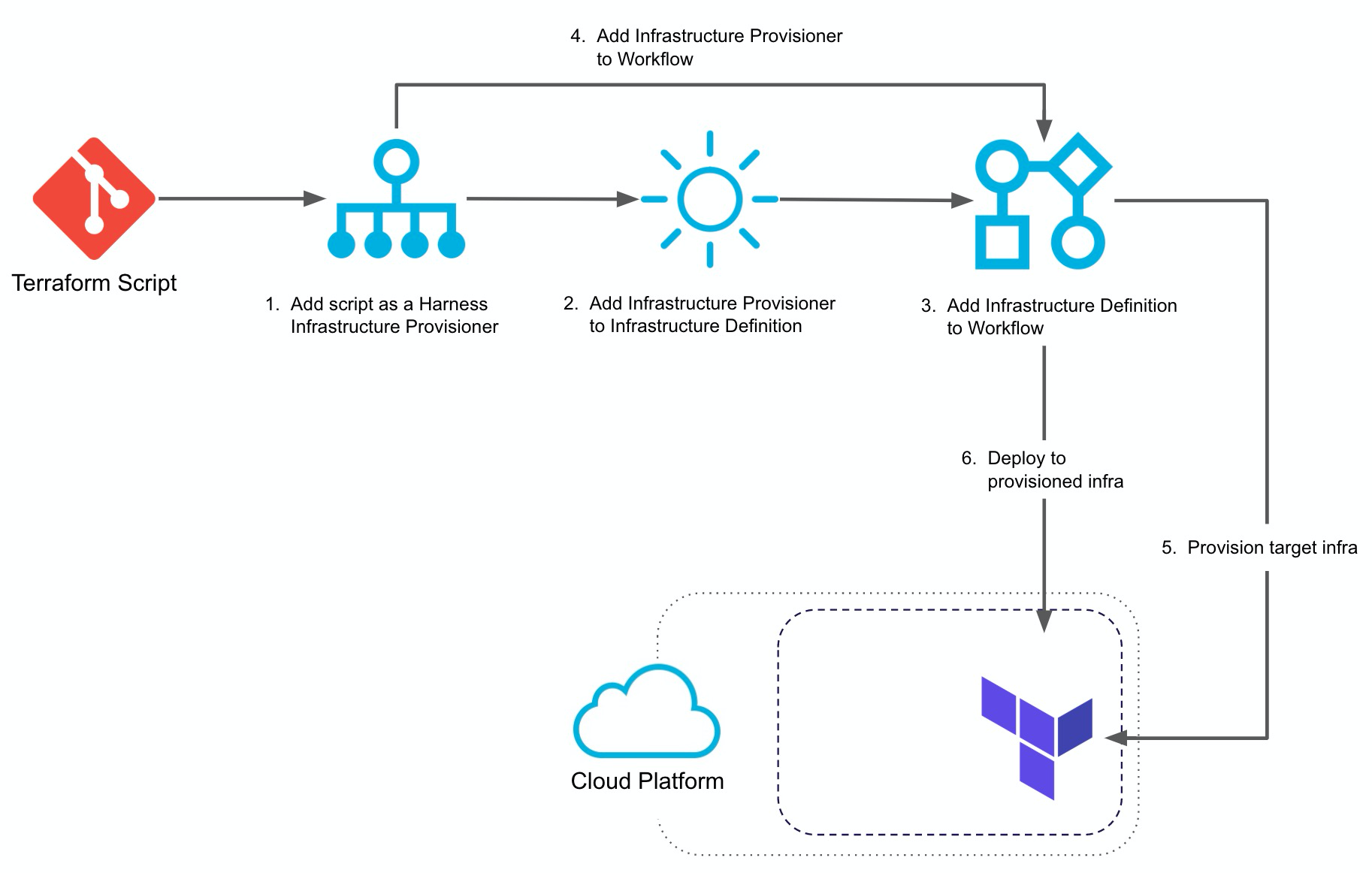
Terraform is popularly used almost across the entire cloud infrastructure landscape today. However, many implementations do not take advantage of the power that Terraform offers. This article highlights ten best practices for improving Terraform implementation; adhering to these practices will help to improve both the quality and the speed of implementation of Terraform projects.
Terraform Implementation – Best Practices
Set Up a Shared State Location Every Time
Terraform works with an intermediary persistent data store that maintains a representation of the cloud infrastructure state. This data store is created when Terraform is first run against a cloud infrastructure account. This store is maintained throughout any subsequent invocations of the Terraform tools. This is because the cloud infrastructure account will not be able to maintain a complete and accurate view of the changes that have been made to it over time. The Terraform state exists to allow Terraform to determine what resources have changed and what changes have to be applied to make the cloud infrastructure match the Terraform code.
Read our blog “Microservice Applications: A New Approach to Building Software”.
Several backend services can be made use of for storing the Terraform state. These include a local file system, a shared file system, a shared object store location, or a relational database. Whichever the choice, a best practice is to use a single common backend location no matter how many developers are working on the infrastructure code.
It is also vital to use any one of the different locking mechanisms that are available to make sure that only one infrastructure provisioning operation is in operative mode at any given time. Having many copies of the Terraform state will likely culminate in infrastructure code drift and collisions. Maintaining the Terraform state in a single shared location also allows the secondary benefit of being able to enforce security and authorization restrictions on who has the permission to update the infrastructure and how they can do it.
Separate State Locations must be Based on Logical Environment Boundaries
Terraform does not have any opinions about how your infrastructure code is organized. It allows the implementation of single large structures that describes all your cloud resources across different environments to small, atomic components provisioned and tracked individually.
However, it is best practice to group related resources based on environment or application. Maintaining a separate Terraform state location for each grouping will practically mean that the number of state locations will proliferate. However, this strict logical separation between environments and applications improves performance and prevents any conflicts.
Download and read our Ebook “MICROSERVICES- A Short Guide Book”.
For example, if you want to host an ERP and a CMS system out in the cloud, and if each of them has a test, staging, and production environment, there would be six separate Terraform state locations.
The Terraform Code has to be Decomposed and Abstracted for Maximum Reuse
Terraform code can also be written poorly or written well. If poorly written, the infrastructure code is likely to be slow, full of bugs, and difficult to maintain. All the principles like DRY, the Single Responsibility Principle, etc., also apply to infrastructure code.
You can break your Terraform code into modules and atomic infrastructure components with well-defined inputs and outputs for better design. You can then use these modules as reusable components that are tailored to your application.
Looking for the best microservices vendor? Give us a call today!
Be Careful when Generating Resource names Programmatically
You have to be careful when you use an algorithmic approach to dynamically generate resource names such as environment, application, and region names for compute instances when using Terraform. Problems could arise when you may have to change the algorithm.
Terraform is loosely coupled to your cloud infrastructure and the platform does not maintain consistent information about what has changed in the provisioned resources. Therefore, Terraform can't manage adequately when the name of a resource is changed.
In this case, you will have to manually rename all the compute instances to match any new naming convention or destroy all of them and allow Terraform to create a new set of names. This can get confusing and dangerous when very low-level modules are reused by several applications across the enterprise.
Read our blog : Microservices architecture and distributed tracing
Therefore, if you require dynamic naming, it is best to handle the naming logic in the composite application module than at low-level resource module levels.
Keep modules and the Environment Implementation Code Separate
You should not only separate your logic into modules and maintain a separate state/environment and application, but you should locate the Terraform module code and provisioning code separately. It is best to do this by maintaining modules in their Git repositories and maintaining an individual Git repository for each environment that has to be provisioned. Easy reuse and collaboration are possible when you maintain your module library and environment-specific code separately.
Strictly review Terraform Validate and Plan Outputs before allowing any Terraform Changes to be Applied to an Environment
This is fairly straightforward but is overlooked most of the time for the sake of quick implementation. Two Terraform tool actions that are critical to successfully implementing Terraform are validate and plan. The validate action checks the syntax of your Terraform code to make sure that it is syntactically valid. There is no comparison to the current state and does not list the resources that will be created or modified by the code. Infrastructure developers should use this action regularly to verify that their Terraform code syntax is correct.
Read our blog : Why is Transaction Management better with Microservices
The Terraform plan action examines your environment’s remote state and lists out the changes to be applied when executing it against your remote environment with the help of the code. Executing and reviewing this command’s output is an important step for any infrastructure-as-code pipeline to trap and resolve issues in the code before modifying your cloud environment.
Summary
Following best practices during Terraform implementation can help you to avoid any pitfalls in its usage and smooth the function of the fully automated infrastructure-as-code pipeline.
Start your microservices journey today! Give us a call!
SayOne and Microservices Development
At Sayone, we design and implement microservices systems that do not have complex architectural layers, and this enables the services to deliver exceptionally fast performance. Moreover, we provide services that are significantly decoupled, allowing you to launch independent services and not end up with the usual inter-dependent microservices that work more or less like a monolith.
We design the microservices keeping in mind the margin required to allow for the transitioning into the new system of your organization’s legacy architecture as well as expanding into the cloud system. Our microservices comprise lightweight code and we provide competitive pricing options for our clients.
Our microservices are built according to the latest international security guidelines that ensure the complete safety of all the data. We also ensure that we deliver the services within stipulated deadlines and we always assure a quick turnaround time for our clients. Equipped with the best infrastructure and the latest tools and technologies, our expert developers will provide you with the best microservices that are easily scalable, enabling a good ROI in the shortest period.
Share This Article
Subscribe to Our Blog
We're committed to your privacy. SayOne uses the information you provide to us to contact you about our relevant content, products, and services. check out our privacy policy.




